Why Are Data Masking Techniques Essential for Tech-Driven Businesses?

In today’s digital landscape, with data breaches on the rise, protecting sensitive information is crucial. A recent report shows that the global average cost of a data breach has surged to $4.35 million.
This eye-opening figure underscores the critical need for businesses, especially tech-driven ones, to safeguard sensitive information like personally identifiable information (PII), financial data, and proprietary information through robust data masking techniques.
The Critical Role of Data Masking in Modern Business
Protecting Sensitive Information
Data masking is a potent tool for securing sensitive data by obscuring or substituting it with fictitious yet realistic data, rendering it unusable for malicious actors. This not only prevents unauthorized access but also mitigates the potential impact of data breaches. As businesses continue to amass vast amounts of sensitive data, implementing effective data masking strategies has become essential.
Regulatory Compliance
Beyond the financial implications, regulatory compliance is another driving force behind the adoption of data masking. Non-compliance with data privacy regulations such as the General Data Protection Regulation (GDPR) can result in severe fines, up to €20 million or 4% of global annual revenue.
Similarly, the Health Insurance Portability and Accountability Act (HIPAA) and the California Consumer Privacy Act (CCPA) mandate strict data protection measures. Data masking helps businesses meet legal obligations, protect customer data, and avoid costly penalties and reputational damage.
Enhancing Security and Mitigating Risks
Reducing Data Breach Impact
While compliance is crucial, the practical benefits of data masking in enhancing security cannot be overstated. A report highlighted that a significant percentage of data breaches involve compromised credentials, making it imperative for businesses to minimize the impact of such breaches through effective data masking. By obscuring sensitive data, even if a breach occurs, the data remains unusable, significantly reducing the potential harm to both the business and its customers.
Cost Efficiency
The financial toll of data breaches is significant, with estimating the average cost at $9.44 million. Implementing data masking helps businesses mitigate these costs and protect their bottom line.
The expenses associated with data breaches, such as fines, remediation efforts, and loss of customer trust, can be significantly reduced, leading to long-term cost savings and improved profitability.
Data Masking Techniques and Their Applications
Data masking techniques are essential tools for securing sensitive data and ensuring compliance with data privacy regulations. These techniques involve obscuring or substituting sensitive information with fictitious yet realistic data, rendering it unusable for malicious actors.
Types of Data Masking Techniques
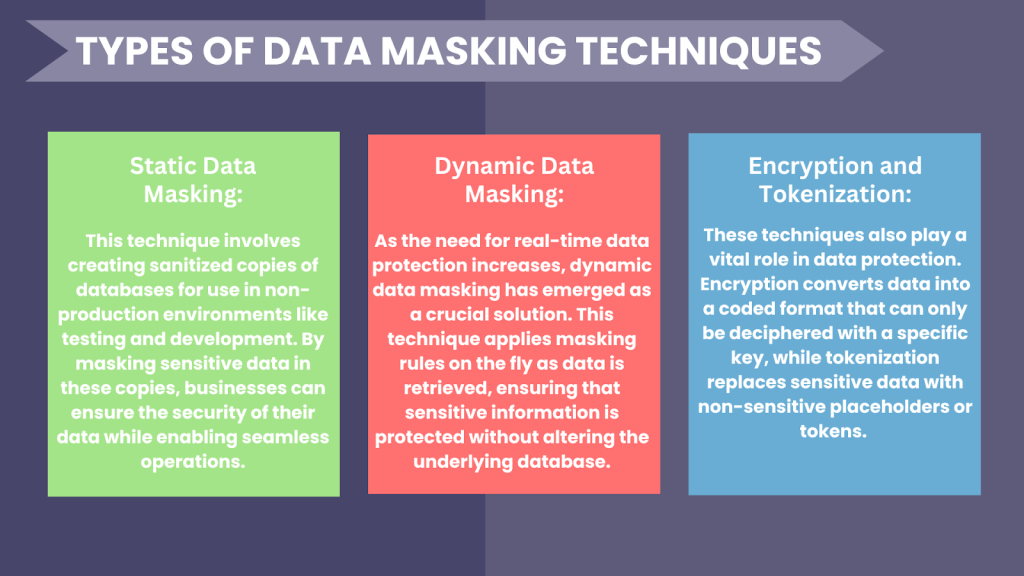
Use Cases in Various Industries
Healthcare: Protecting patient data while enabling research and operational efficiency is a critical challenge in the healthcare industry. Data masking techniques secure sensitive patient information, such as medical records and personal details, while allowing healthcare providers to use data for research, analytics, and improving patient care.
Finance: The financial sector deals with a vast amount of sensitive data, including financial transactions and client information. Data masking is essential for securing this information and maintaining customer trust. By obscuring sensitive data, financial institutions can mitigate the risks of data breaches and ensure compliance with relevant regulations.
E-commerce: In the e-commerce realm, customer data is a valuable asset that must be protected during transactions and throughout the customer journey. Data masking techniques safeguard sensitive information like payment details, addresses, and personal identifiers, enhancing customer trust and minimizing the risk of data breaches.
Best Practices for Implementing Data Masking
Data Discovery and Classification
Before implementing data masking techniques, it is crucial to identify and categorize sensitive data. Thorough data discovery and classification are paramount. This process ensures that all sensitive information is accurately identified and appropriately masked, reducing the risk of inadvertent exposure.
Choosing the Right Technique
Selecting the appropriate data masking technique depends on several factors, including data sensitivity, security requirements, and cost implications. Organizations need to adopt multiple techniques based on data sensitivity and use cases, ensuring tailored and effective protection.
Continuous Monitoring and Auditing
Implementing data masking techniques is not a one-time solution; it requires ongoing vigilance. Continuous monitoring and auditing are essential to ensure that these techniques remain effective and up-to-date, preventing any potential data leaks or security breaches. Regular audits and updates are necessary to address evolving threats and maintain robust data protection.
Future Trends and Challenges
Integration with AI and Machine Learning
Looking ahead, the integration of Artificial Intelligence (AI) and Machine Learning (ML) with data masking techniques is set to revolutionize data security. AI and ML can enhance data masking by automating the process of identifying and classifying sensitive data, as well as predicting potential vulnerabilities and adapting masking techniques accordingly.
Balancing Security and Usability
Despite these advancements, balancing security and usability remains a challenge, underscoring the need for effective and user-friendly data masking strategies. As businesses strive to protect sensitive data, they must also ensure that legitimate data access and usability are not hindered, maintaining operational efficiency and productivity.
FAQs
How does data masking differ from encryption?
Data masking substitutes sensitive data with fictitious but realistic data, whereas encryption converts data into a coded format that can only be deciphered with a key. While encryption maintains the original data format, data masking obscures the data itself, rendering it unusable for unauthorized individuals.
Can data masking affect application performance?
Properly implemented data masking should not significantly impact application performance, especially with optimized techniques like static and dynamic masking. However, some techniques like encryption and tokenization may introduce a performance overhead, which can be mitigated through careful implementation and optimization.
Is data masking a foolproof method for data protection?
No, data masking is not foolproof. It hides data but doesn’t eliminate it.
Conclusion
Ultimately, data masking is essential for tech-driven businesses, offering a robust solution to protect sensitive information, ensure compliance, enhance security, and mitigate financial risks.
By staying ahead of trends, adopting best practices, and leveraging emerging technologies like AI and machine learning, businesses can navigate the complex landscape of data protection with confidence, fortifying their security posture and maintaining a competitive edge.